When we asked a group of CIOs in the Southern California region what their biggest concern was for the immediate future, their answer was clear: cybersecurity and social engineering; the culmination of people, process, and technology.
Link: Read about the relationship of people, process and technology in IT project management.
In 2016 alone, the FBI received nearly 300,000 cybersecurity fraud complaints categorized as Business Email Compromise (BEC), totaling over 1.4 billion in economic losses. Furthermore, these cyber attacks were recorded in all 50 states and over 131 countries. As cybersecurity continues to become the number one threat for both small and large companies, all employees must be educated and trained on social engineering and its related counterparts to mitigate a potential crisis.
Business Email Compromise
The FBI has monitored Business Email Compromise (BEC) since 2013, but the increased complexity and use by criminal organizations is said to be unprecedented. Additionally, the FBI calculated a 1,300 percent increase in identified loses attributed to BEC; the real number, including unidentified losses, could be double. BEC fraud has become big business for criminal groups who have perfected their deception methods, making it nearly impossible for employees to protect themselves without education, training, and protocol. Although the culprits use many tactics, they’re keen on exploiting the human component (the employee) in this process. From gaining access to a company’s systems to deploying malware and impersonating C-level management, scammers have the upper hand; good enough reason for a company to invest in their most important cybersecurity measures: their people.
Special Agent Martin Licciardo, a veteran organized crime investigator at the FBI’s Washington field office, explains, “BEC is a serious threat on a global scale, and the criminal organizations that perpetrate these frauds are continually honing their techniques to exploit unsuspecting victims.”
The Human Component of BEC
Humans are a company’s most valuable asset, but they’re also the most vulnerable. Defined by TechTarget, social engineering is a planned method of tricking people into breaching security procedures using human interaction, often well-planned email, text, or mobile communication to deceive the message recipient. Unfortunately, these recipients are usually employees who can be targeted by scams and exploited through impersonation — cue the call from the CEO… who is on travel and needs to reset his “new” password immediately, or else…
Another common but more discrete scenario involves a well-trusted vendor emailing (or calling) financial staff referencing the correct names and partial account numbers to have an invoice paid. The fact is, there are many possible ways to trick people into doing something they wouldn’t do under normal circumstances. All it takes is some quality research.
Although many cyberattacks of this nature go unreported, they are still one of the most common forms of cybercrime, and therefore a major vulnerability to any company. A CIO can lead a transformation in cybersecurity by investing in critical software tools and the technical expertise of security specialists. Still, without detailed testing, education, and response plans for employees on all levels, their company will encounter an attack that can derail progress and diminish trust. If a company hopes to protect its systems and people from fraud, it must become proactive with security measures, a process that includes educating employee groups.
Common Forms of Social Engineering
Social engineering is a decades-old form of cybercrime. Its focus on human interaction as a touchpoint to valuable data and information is the factor that makes it a choice method among cybercriminals. The chances are good that every employee of a large company will witness social engineering at some point in their career.
Although the goal is to prevent exposure to the threat if a breach does happen, companies must prepare their workforce to ensure it doesn’t happen a second time. So whether employees are aware of this threat or are finally receiving the proper training, these are the factors that need to be monitored constantly.
Baiting
Free trials is hard to resist, especially with digital products and services. A complimentary download of information that provides instant gratification is equally hard to resist. And to think, all you have to do is enter some basic information like login credentials — harmless, right? Quite the opposite. This seemingly simple exchange of information makes baiting a widely used social engineering tactic. Not only is it incredibly easy to deceive someone for their information, it’s challenging to determine what’s real and what is not. As more and more data is collected and shared online, it becomes easier for suspects to target new victims using identified interests. Those that spike their interest and ever so slightly make the person feel as though there is little risk involved.
Did you know that baiting is a physical form of scamming as well? Here’s a scenario to think about:
You are leaving a company meeting when you see a small box of cool looking flash drives. A sign nearby reads, ’employees only, please take only one.’ So you do. You take it to your desk where you plug it in and begin organizing files. Unfortunately, the box of free drives was placed there for a reason. And that reason is now “crawling” its way through the company network.
Phishing
Similar to baiting, phishing is a tactic used to persuade people to trust a source of information. The information looks authentic but is loaded with malware. Here’s how it works:
A malicious party sends a fake email that looks identical to what you receive from a company you shop with. By opening this email, or worse, clicking on the content it contains, a person’s computer is compromised. As the name implies, phishing involves casting a wide net to catch as many people (and their data) as possible. For large, highly interconnected organizations, it can cause severe long-term damage.
How would you do when presented with a phishing attempt? The University of California Berkeley recently shared examples of the phishing techniques used on their staff and students. Even experienced employees would be fooled by these techniques:
Google Doc Invite (With nearly every student on campus using Google Docs, can you imagine the number of them who clicked?)
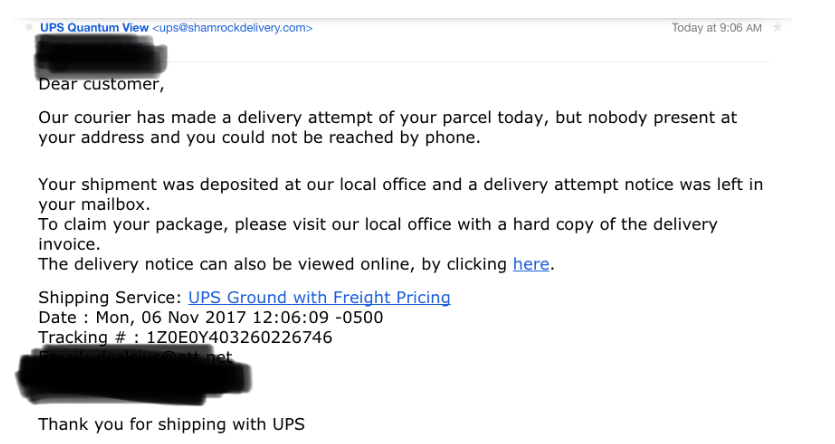
As though the timing couldn’t have been better, we received an email from UPS just moments ago that nearly fooled us:
Now, when viewing emails such as the one above on mobile, you rarely see the sender’s address; the subject line is prominent. It just so happens that we were expecting a package today, which made this more believable. But thanks to our recent refresher course on social engineering, we refrained from opening and reported this email to UPS.
Pretexting
More of a targeting approach for stealing personal information, pretexting involves attackers who impersonate others and fabricate scenarios, or request information and access to a database by developing trust and rapport with employees by identifying themselves as someone else. Often, the stories that criminals create are elaborate and contain much more detail than phishing or baiting. Especially true for organizations with little planning in place, it’s not uncommon for subordinates to fall victim to this trap in fear of second-guessing management.
Pretexting differs from many other tactics in that this method requires significant trust to be gained by the malicious party, and they must also have some sort of credibility established in their operation to initiate conversations in the first place. When viewing pretexting from an IT perspective, scammers tend to play the role of an external IT services provider. They will request information on internal employees related to a specific project. The more information they collect, the more chances they have to access company systems. It’s a game of building trust using fabricated identities. So, how does a company protect its employees from an event like this? Training!
Tailgating
A form of cyberattacks that we don’t often discuss is one where a person steals employee credentials (from their computer or via their badge) and follows other employees into a secured building where they carry out their plan. For mid-size to large organizations, it’s difficult to account for every employee at all times. Even employees can’t always tell if another person is an employee, contractor or visitor, making it easier for a trespasser to access a building where vital information is stored.
So, how would tailgating look in action? A common scenario, the driver for a shipping service or third-party provider targets workers as they enter the building. As soon as an authorized person opens the door, the intruder will request a door hold as they carry in packages, food, or supplies.
Scareware
Relatable to phishing, scareware pops-up on a computer screen in the form of a security offer or program update portraying a virus on your system. By scaring the user into thinking their machine is infected, they either download the faux program or call an “agent” to purchase software that can remove the infectious files. Unfortunately, they’re giving away their data and installing malware on their system and possibly an entire network — cue the crisis.
Social Engineering in Social Media
Social engineering has prevailed as a cyber-security threat for many years and doesn’t show signs of slowing down. As it stands today, growth across Facebook, Twitter, and LinkedIn lends a helping hand to the many forms of social engineering. It allows scammers to refine their deceptive techniques to flourish among the masses. The allure of larger networks and a greater sense of connection and influence makes it more difficult for organizations to prevent a cyberattack. On social networks, in particular, content is shared at a rapid rate and in large quantities. With one wrong click, a seemingly innocent piece of content can turn catastrophic when it provides access to personal information or a network of users.
This nuance in cybercrime from predominantly email to a new, social-driven world, has paved the way for a modern form of social engineering, better known as social media engineering. Where other forms of hacking deal with computer security-systems, social media engineering exploits human-to-human forms of communication over a digital network and does so with a higher frequency and success rate than traditional methods.
A company that specializes in digital and social media security, Zerofox reiterates that social media enables malicious parties to have one-to-many conversations rather than one-to-one, using an alias (often a very realistic social media profile or company account). Companies must think about the safety of every employee, especially those who are active on social channels. A by-product of network-based platforms, social media opens the door for attackers who wish to connect with every employee of a business. The door doesn’t need to be an office computer. Every employee (within the scope of their job, mainly computer-dependent), must question the content they see, taking caution always. For the few C-level executives who have direct ownership over security prevention (Chief Information Security Officer, CISO), it’s now their responsibility to familiarize corporate teams with social media security just as they do with email security.
Penetration Testing
With a focus on social engineering and BEC, awareness is the best line of defense for both small and large companies. Although one responsibility of the CIO/CISO is to understand the impact of cybersecurity on the organization, they too must adapt to evolving threats and promote awareness as a top priority among their employee groups, especially true for the personal nature of social engineering. In other words, complete reliance on spam filters and defense software won’t mitigate the danger that lurks near every employee within the company. In essence, the best target is always the unsuspecting target. Promoting a modern mindset that enables every employee to embrace a responsibility towards understanding information security at a foundational level is a clear opportunity for companies, and it can position a company to be two steps ahead of the closest threat.
Promoting and building awareness around cybersecurity — an identified objective for the CIO — is the means to an educated workforce and the first line of defense against cyber threats. Using webinars, meetings, and clinics, information officers have a simple toolkit at their disposal, one that engages employees, facilitates learning, making them a valuable asset.
Together, leaders and team members should use mock simulations for scenarios that employees may face, a realistic exercise that people can memorize and recognize when they encounter a threat. This is especially helpful for new employees as they are likely to be the ones first targeted through social engineering. Similar to a self-defense class, the idea is to understand the processes involved in the prevention of a security breach using consistent practice.
It’s common for security officers to share newsletters that explain scam tactics. The training and education resources help companies establish protocols for handling urgent cybersecurity issues across the company.
Lastly, security officers encourage the use of social engineering penetration tests (also known as pen tests). These tests are proven to provide immediate feedback on employees’ ability to recognize and respond to threats as well as follow identified procedures set my management.
Penetration tests help determine how easily employees are deceived by an outside party and provide transparency to security objectives for management to pursue. Although security officers agree that people are the weak link — due to vulnerability — companies that prepare their workforce to avoid cyber threats have a significant advantage over their competition.
From Education to awareness and acceptable use, the path forward is clear for CIOs’: Social engineering remains a credible threat that must be addressed. Especially true for identifying new talent, a person’s aptitude for understanding the importance of cybersecurity is a valuable and highly desirable asset.